1) Algorithm process
The overall algorithm is divided into three steps: 1) Each node transaction randomly selects some transactions, and the total number of transactions of all nodes is B. The transaction of each node is encrypted to generate x. 2) Broadcast the encrypted transactions of each node through the ACS protocol, and form a unified transaction sequence. 3) Decrypt transactions to generate blocks. The overall algorithm flow is as follows:
2) TPKE encryption and decryption algorithm
TPKE, threshold public key encrypTIon, encryption and decryption algorithm, one public key, multiple private keys. Data encrypted by TPKE requires multiple sub-keys to decrypt.
TPKE.Setup creates the public key PK and several sub-keys SKi. TPKE.Enc encrypts m with PK, and the encrypted result is C. TPKE.DecShare decrypts the intermediate result with a single subkey. TPKE.Dec decrypts m with several intermediate results.
3) ACS protocol
ACS - Asynchronous Common Subset. The ACS protocol is composed of two protocols: the RBC protocol and the BA protocol. The main function of the ACS protocol is to broadcast transactions through the RBC protocol, and then form a consistent list through the BA protocol. The basis of data consensus among network nodes is the RBC protocol.
4) RBC protocol
RBC, reliable broadcast protocol. The RBC protocol reduces the data transmission between nodes through the erasure coding algorithm. After two broadcasts (ECHO and READY messages), a consensus can be formed between network nodes. The algorithm of RBC is as follows:
The essence of the RBC algorithm is to make full use of the network bandwidth between all nodes. The broadcast initiator P divides the data (blocks) to be broadcast into N parts (2f of which are redundant) through the erasure coding algorithm and distributes them to N nodes. These split data are broadcast between nodes using their own network bandwidth. The advantage of this is that the network bandwidth of the broadcast initiator P is reduced, and the network bandwidth of all nodes is fully utilized, as shown in the following figure:
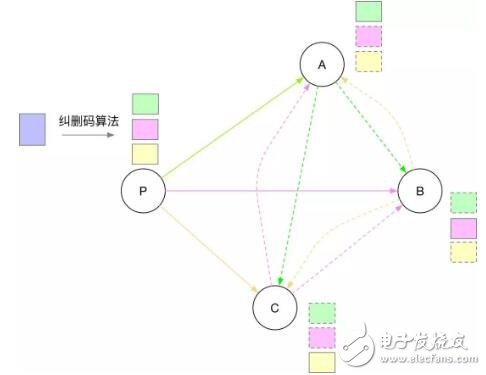
In the above figure, the broadcast initiator first broadcasts the divided small blocks generated by the erasure coding algorithm to the three network nodes A, B and C. After receiving the small block data, network nodes A, B and C broadcast it to other nodes. Any node can recover the original block as long as it receives more than a certain number of small blocks.
5) Complexity and experimental data
The paper points out the overall data transfer complexity of the HoneyBadgerBFT algorithm:
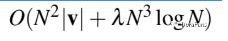
where v is the maximum data size on a single node. The derivation method is shown in the following figure:

Because one transfer implements B transactions (N^N*LogN), the complexity of the transfer amount of one transaction can be approximated as O(N).
The paper simulates nodes on the Amazon cluster and compares the performance of HoneyBadgerBFT and PBFT, as shown below:
Simply put, in the case of few network nodes (for example, 8 nodes), the performance of HoneyBadgerBFT is slightly inferior to the PBFT algorithm. However, when the number of network nodes increases, the performance of the HoneyBadgerBFT algorithm is almost unchanged, while the performance of the PBFT algorithm decreases significantly.
Summary: HoneyBadgerBFT is a consensus algorithm designed for asynchronous networks. The HoneyBadgerBFT algorithm allows network nodes to broadcast transactions at the same time, and its core is the RBC broadcast protocol. The main idea of ​​the RBC broadcast protocol is to use the erasure code algorithm to reduce the amount of data transmission between nodes, and to form a consistent transaction list through the BA algorithm. The paper points out that the complexity of the HoneyBadgerBFT algorithm is O(N). In the case of fewer network nodes (for example, 8 nodes), the HoneyBadgerBFT performance is inferior to the PBFT algorithm. However, when the number of network nodes increases, the performance of the HoneyBadgerBFT algorithm is almost unchanged, while the performance of the PBFT algorithm decreases significantly.
SHENZHEN CHONDEKUAI TECHNOLOGY CO.LTD , http://www.siheyidz.com